OAuth2 is an industry-standard authorization framework that enables secure access to resources on behalf of a user without exposing their credentials. It’s widely used for allowing users to authenticate with third-party services (such as Google, Facebook, or GitHub) and grant limited access to their resources without sharing their passwords.
Implementing OAuth2 in web and mobile applications is essential for enabling secure, delegated access. This article explores the basics of OAuth2, its workflow, and how to integrate it into web and mobile applications.
1. What is OAuth2?
OAuth2 (Open Authorization 2) is a framework that provides applications the ability to authenticate users and access resources on their behalf. OAuth2 does not authenticate the user directly but provides a mechanism to grant applications limited access to resources. This method avoids the need for sharing passwords or storing sensitive credentials, making it a secure and scalable approach for authorizing users.
OAuth2 is often used in scenarios where third-party apps or services need access to user data stored on another platform, like logging into a website using your Google or Facebook account.
2. Key Concepts of OAuth2
2.1 Roles in OAuth2
OAuth2 involves several key roles:
- Resource Owner (User): The person who owns the data or resources.
- Client (Application): The application requesting access to the resources.
- Resource Server: The server hosting the resources (e.g., Google, Facebook).
- Authorization Server: The server responsible for authenticating the resource owner and issuing access tokens (e.g., Google’s OAuth server).
2.2 Tokens
- Access Token: A token that the client uses to access protected resources on behalf of the user.
- Refresh Token: A token that the client can use to obtain a new access token when the current one expires.
2.3 OAuth2 Grant Types
OAuth2 offers multiple authorization flows, known as “grant types,” to accommodate different use cases:
- Authorization Code Grant: The most common type used for server-side applications. It provides security by not exposing access tokens directly to the client.
- Implicit Grant: Mainly used for single-page applications, where tokens are issued directly without an authorization code.
- Password Grant: Used in cases where the resource owner’s username and password are provided directly to the client, which is not recommended due to security risks.
- Client Credentials Grant: Used for server-to-server communication without user intervention.
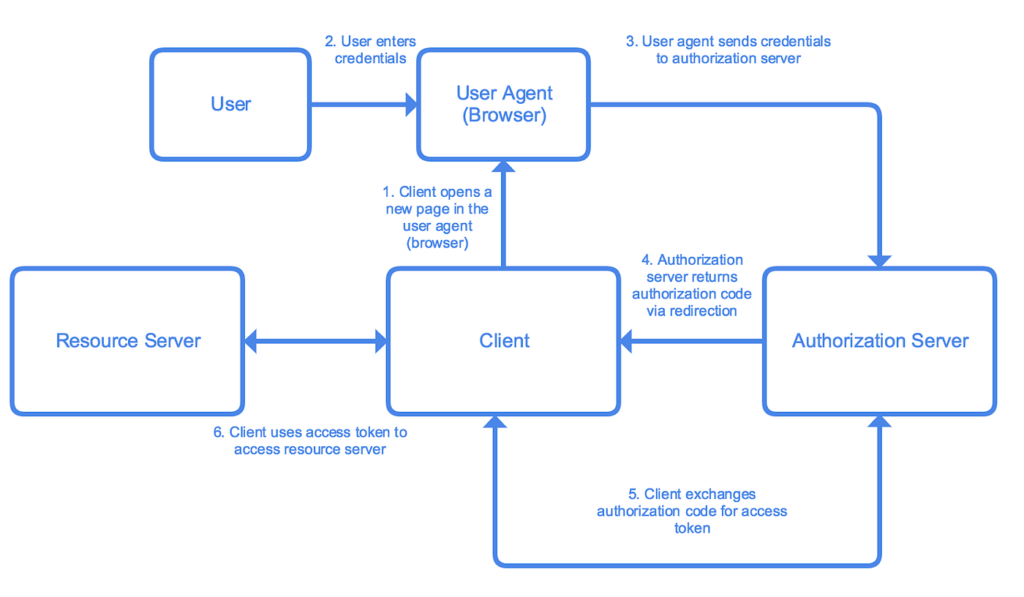
3. OAuth2 Workflow for Web Applications
In web applications, OAuth2 typically follows the Authorization Code Grant flow, which is the most secure. Here’s how it works:
- Authorization Request: The client (web app) redirects the user to the authorization server (e.g., Google), asking for permission to access their resources.
- User Approval: The user logs in and grants permission for the app to access their data.
- Authorization Code: After approval, the authorization server redirects the user back to the web app with an authorization code.
- Token Exchange: The web app sends the authorization code to the authorization server, exchanging it for an access token and, optionally, a refresh token.
- Access Resources: The web app can now use the access token to access the user’s resources on the resource server (e.g., Google API).
- Token Refresh: If the access token expires, the web app can use the refresh token to request a new access token without re-authenticating the user.
3.1 OAuth2 Integration in Web Applications
To implement OAuth2 in a web application, follow these steps:
- Register Your Application: Register your web app with the OAuth2 provider (e.g., Google Developer Console, Facebook Developers). You’ll get a client ID and client secret.
- Redirect URI Setup: Configure the redirect URI to receive the authorization code after user consent. The redirect URI must match the one registered with the OAuth provider.
- Initiate Authorization: When the user clicks “Sign in with Google,” redirect them to the authorization server (Google’s OAuth server).
- Handle Authorization Code: Once the user grants access, capture the authorization code returned to your redirect URI.
- Exchange Code for Token: Send the authorization code to the OAuth provider’s token endpoint to get an access token.
- Make API Requests: Use the access token to make authorized API requests to access user data.
Example:
// Redirect user to Google for authentication
window.location.href = 'https://accounts.google.com/o/oauth2/auth?client_id=YOUR_CLIENT_ID&redirect_uri=YOUR_REDIRECT_URI&response_type=code&scope=email profile';
// Handle callback after user approves
app.get('/auth/callback', async (req, res) => {
const { code } = req.query;
const response = await axios.post('https://oauth2.googleapis.com/token', {
code,
client_id: 'YOUR_CLIENT_ID',
client_secret: 'YOUR_CLIENT_SECRET',
redirect_uri: 'YOUR_REDIRECT_URI',
grant_type: 'authorization_code',
});
const { access_token } = response.data;
// Use access token to access user data
});4. OAuth2 Workflow for Mobile Applications
OAuth2 is similarly implemented in mobile applications, with a few differences due to the mobile environment. For mobile apps, the Authorization Code with PKCE (Proof Key for Code Exchange) is the recommended flow. It is an extension of the Authorization Code Grant designed for public clients (like mobile apps) that can’t securely store a client secret.
4.1 PKCE Flow
- Generate Code Challenge: The mobile app generates a code verifier and a code challenge (a hashed version of the code verifier).
- Authorization Request: The app redirects the user to the authorization server with the code challenge.
- User Approval: The user logs in and approves access.
- Authorization Code: The authorization server returns the authorization code to the app.
- Token Exchange with Code Verifier: The mobile app exchanges the authorization code for an access token by sending the code verifier.
- Access Resources: The app can use the access token to access the user’s resources.
Example:
const codeVerifier = generateRandomString();
const codeChallenge = base64urlencode(sha256(codeVerifier));
// Redirect user to authorization server
window.location.href = `https://accounts.google.com/o/oauth2/auth?client_id=YOUR_CLIENT_ID&redirect_uri=YOUR_REDIRECT_URI&response_type=code&scope=email profile&code_challenge=${codeChallenge}&code_challenge_method=S256`;
// Handle callback and exchange code for access token with code_verifier5. Benefits of Using OAuth2
5.1 Secure Access
OAuth2 allows users to grant specific permissions to apps without sharing their credentials. This reduces the risk of exposing passwords to third-party applications.
5.2 Granular Permissions
With OAuth2, users can grant limited access to their resources, such as allowing an app to read their contacts but not modify them.
5.3 Scalability
OAuth2 is highly scalable and is used by major platforms (Google, Facebook, GitHub) to authorize millions of users every day.
5.4 Single Sign-On (SSO)
OAuth2 is the foundation of single sign-on (SSO), allowing users to log in to multiple services using one set of credentials.
6. Challenges in Implementing OAuth2
6.1 Complexity
Implementing OAuth2 requires understanding the different grant types and setting up correct flows depending on the type of application (web or mobile).
6.2 Security Risks
Misconfiguring OAuth2 flows can lead to security vulnerabilities. It’s important to implement best practices, such as using PKCE in mobile apps and avoiding storing sensitive data like client secrets on the client side.
6.3 Token Expiry
Handling access token expiry and implementing refresh tokens adds complexity to maintaining user sessions. You’ll need to handle token refresh logic securely.
7. Conclusion
OAuth2 is a powerful and secure authorization framework that enables web and mobile applications to interact with third-party services without sharing credentials. By implementing OAuth2, you can offer your users a secure and seamless login experience with popular services such as Google or Facebook.
At TechsterTech.com, we provide expert guidance in implementing OAuth2 and other secure authentication mechanisms for your web and mobile applications.